GitHub & GitLab
Repositories
View a list of all repositories tagged for Login.gov.
Some repositories in GitHub are mirrored from our self-hosted GitLab.
Applications
-
18f/identity-idp
secure.login.gov
IdP (main application) -
18f/identity-pkiPIV/CAC application -
18f/identity-idp-configService Provider (service_providers.yml) and Agency (agencies.yml) configuration repo that can be updated and deployed independently of the IdP. -
18f/identity-dashboardPartner Dashboard for viewing and editing service provider configurations (only in the INT environment). -
18f/identity-charts(Archived)
login-charts-server.app.cloud.gov
Metrics dashboard for Login.gov
Libraries
-
18f/identity-hostdataGem that provides functionality for our Ruby applications on our EC2 infrastructure to download secrets and read configs. -
18f/identity-loggingGem that sets up common log formatting and configuration for Rails applications -
18F/omniauth_login_dot_govProvides an Omniauth strategy for Login.gov that helps other projects integrate with Login.gov more easily. Some use cases include the identity-dashboard as well as Touchpoints, USMC and search.gov -
18f/identity-validationsGem that provides shared validations for the ServiceProvider model across the IdP and dashboard -
18f/identity-telephony(Archived) Gem that provides a common interface for voice and SMS features across multiple vendor backends. This code has been moved into the IdP codebase. -
18f/identity-doc-auth(Archived) Provides a library for performing document authentication. This code has been moved into the IdP codebase. -
18f/identity-proofer-gem(Archived) Provides a generic interface around identity proofing (IDV, identity verification) that is implemented by other proofers. This code has been moved into the IdP codebase. -
18f/identity-lexisnexis-api-client-gem(Archived) Implementation of the identity-proofer interface for LexisNexis. This code has been moved into the IdP codebase. -
18f/identity-aamva-api-client-gem(Archived) Implementation of the identity-proofer interface for AAMVA for drivers licenses. This code has been moved into the IdP codebase.
Example Applications
-
18f/identity-oidc-sinatraExample service provider that uses OpenID connect and Sinatra. -
18f/identity-saml-sinatraExample service provider that uses SAML and Sinatra. -
18f/identity-saml-rails(Archived) Example service provider that uses SAML and Rails.
Platform and Infrastructure
-
lg/identity-devopsPlatform CLI tools, Terraform for infrastructure as code (IaC), Chef for instance (server) provisioning, and so much more! (Too much more?) -
lg/identity-devops-privatePer-application environment additional Terraform and Chef configurations -
lg/identity-terraformPublicly shared Terraform modules -
lg/identity-cookbooksPublicly shared Chef cookbooks -
lg/identity-base-imageAWS EC2 Image (AMI) definitions and build pipelines to match -
18f/identity-monitor(Archived) Smoke tests and NewRelic scripts that test the site -
18f/identity-lambda-functionsAWS Lambda functions and the code to deploy them - Only used for KMS matching code at this time
Design
18f/identity-design-assetsA place for the Login.gov design team to version and store design assets (illustrations, sketch files, etc.)
Static Sites
-
GSA-TTS/identity-site
login.gov
Hosted on: Cloud.gov Pages
Public marketing page. -
18f/identity-design-system
The Login.gov Design System, an extension of the U.S. Web Design System used on Login.gov sites to consistently identify the Login.gov brand. -
GSA-TTS/identity-dev-docs
developers.login.gov
Hosted on: Cloud.gov Pages
Developer documentation and integration guides for OpenID Connect and SAML. -
18f/connect.gov(Archived)
connect.gov
Hosted on: Cloud.gov Pages
A site to disambiguate the Login.gov’s predecessorconnect.govfrom Connecticut’s ConnectCTconnect.ct.gov -
18f/identity-partners-site(Archived)
partners.login.gov
A site to present information for partners, now exists as/partnersin theidentity-siterepo. -
GSA-TTS/identity-reporting
data.login.gov
Hosted on: Cloud.gov Pages
Public reporting dashboard. -
GSA-TTS/identity-handbook
handbook.login.gov
Hosted on: Cloud.gov Pages
This handbook! -
lg-public/identity-internal-handbook
lg-public.pages.production.gitlab.login.gov/identity-internal-handbook/
Hosted on: GitLab Pages (self-hosted)
Internal version of this handbook (Private to Login.gov team only) -
18f/identity-handbook-private(Archived)
Old, private version of this handbook! (Private to Login.gov team only)
Permissions
Requesting Access
To request access to GitHub:
- Set up GitHub account per TTS GitHub guidelines
- Join the #admins-github Slack channel
- Tag
@github-admins-loginand request to add your GitHub username to the following teams/orgs:
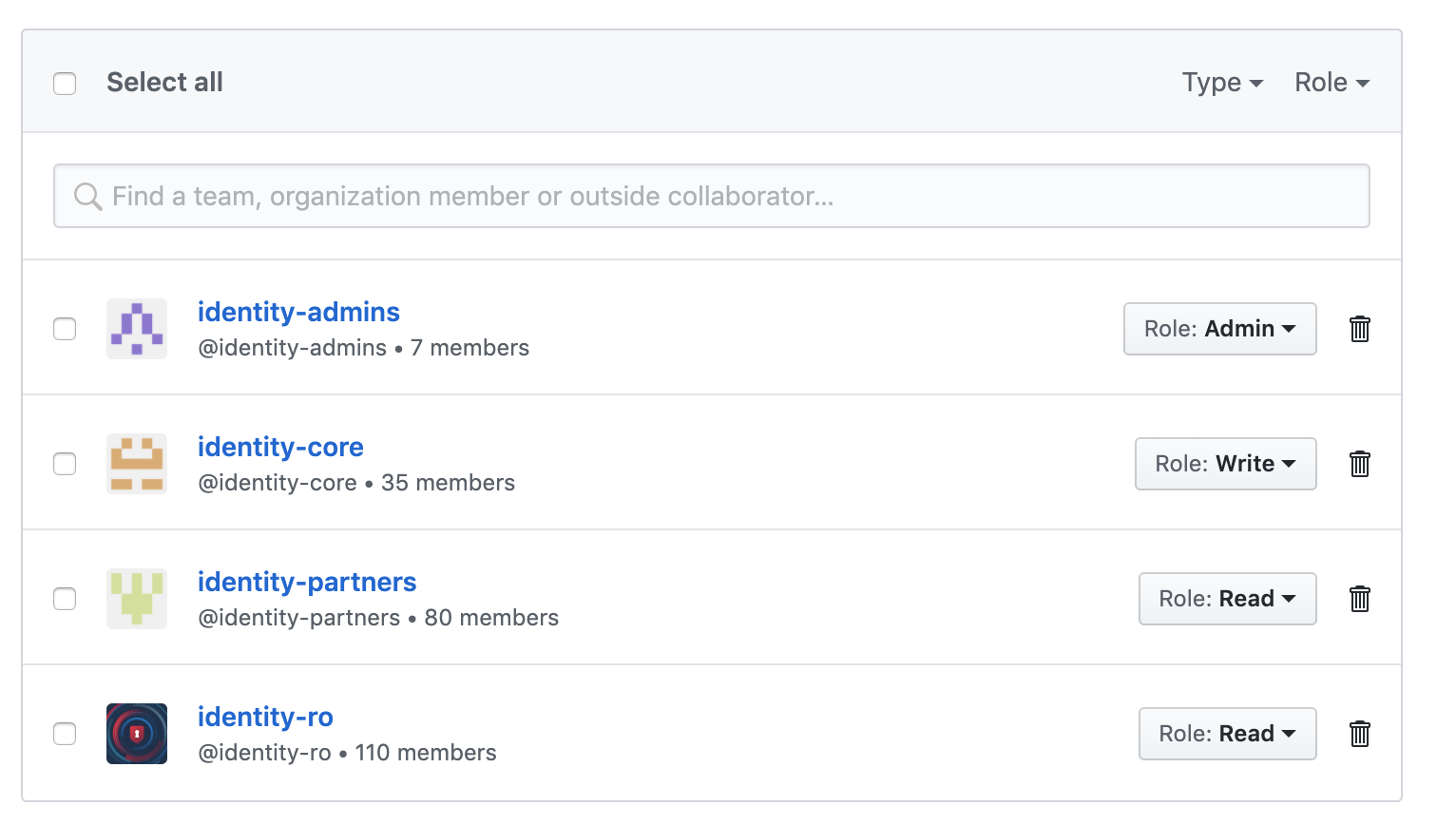
Repository Permissions
All Login.gov repos should have the following permissions. They can be changed by a current admin under “Settings” > “Manage Access” in GitHub.
| Group Name | Role | Applicable Orgs |
|---|---|---|
| identity-admins | Admin | 18f, GSA-TTS |
| identity-core | Write | 18f, GSA-TTS |
| identity-partners | Read | 18f |
| identity-ro | Read | 18f |
We should not have any individual access, only team access.
Workflows
Signed Commits
Repositories hosted in the GSA-TTS org on GitHub (the mostly static sites) require signed commits. See GitHub’s documentation on configuring git to sign commits.
We strongly recommend that you configure git to automatically sign commits (so you don’t have to add -S to every commit)
- The default settings for GPG only prompt for a password once every 10 minutes
- You can set this up globally or per-repo (locally)
-
To verify that the signing has been enabled, in either your
~/.gitconfig(global) or the.git/configin each repository (local), check for these values:[commit] gpgsign = true [user] signingkey = <<YOUR ID HERE>>
Email Notifications and Filters
Default settings for GitHub can generate a lot of email that can be tough to sift through. Here are some strategies for helping manage these notifications:
-
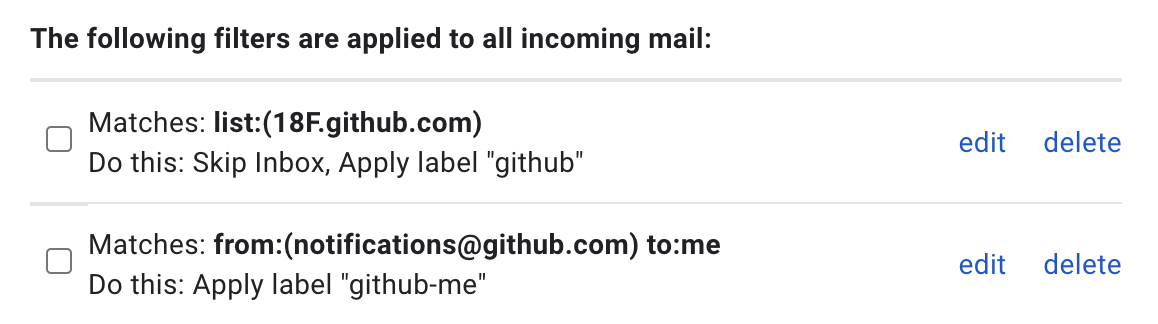
Create Gmail filters to help highlight mentions:
-
A filter to get emails out of the Inbox
list:18F.github.com OR list:gsa-tts.github.com
Skip Inbox, Apply label: github -
A mentions/me filter to highlight Pull Requests you’re participating in (such as being tagged as a reviewer)
from:notifications@github.com to:me
Apply label: github-me
Example:
-
-
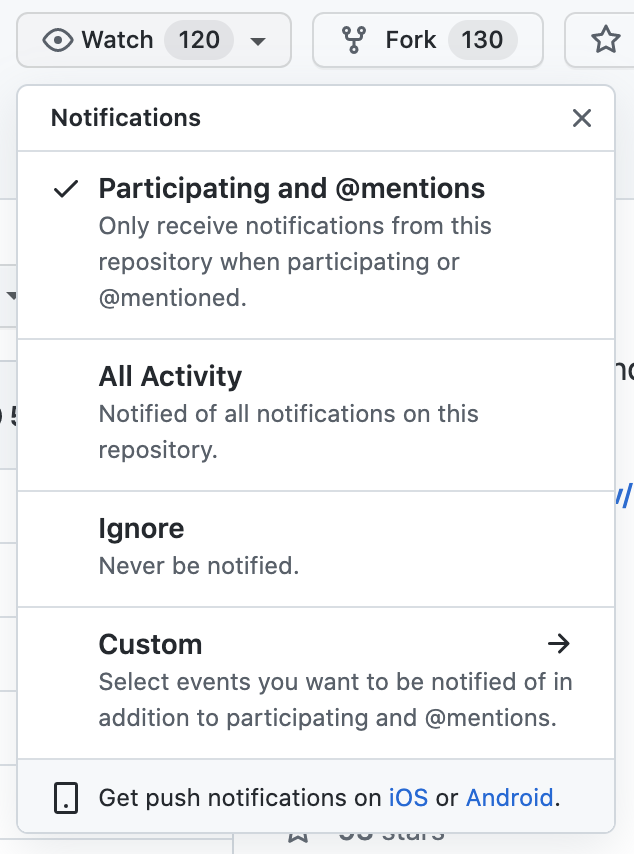
In GitHub, only have notifications on for repositories you care about (unwatch all others). The 18F org has many repos that do not affect Login.gov. For example, set up “All Activity” for
identity-repos, and “Participating” for all others.Key Repositories Other Repositories 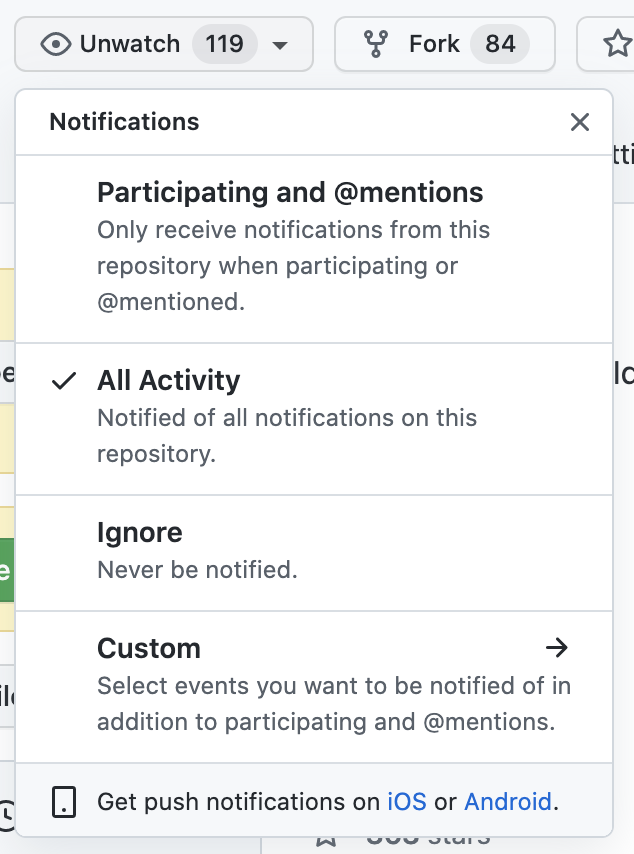
Running CI Outside of a Pull Request
Engineers may want to run CI before submitting their code for review. For example, this can be a helpful way to check that all tests pass. To run CI on a branch without creating a pull request:
- Push the up to date branch to GitHub
- Navigate to https://gitlab.login.gov/lg/identity-idp/-/pipelines/new
- In the drop-down below
Run for branch name or tag, select the branch for which you’d like to run CI
Sharing Work With Other Engineers
Engineers might want to share work with other engineers, such as before starting a pairing session. To share work without creating a PR, consider using GitHub’s “compare” feature.
- Push the up to date branch to GitHub
- From the repo’s home page, select the branch
- Click “Contribute” and select the left button, “Compare”
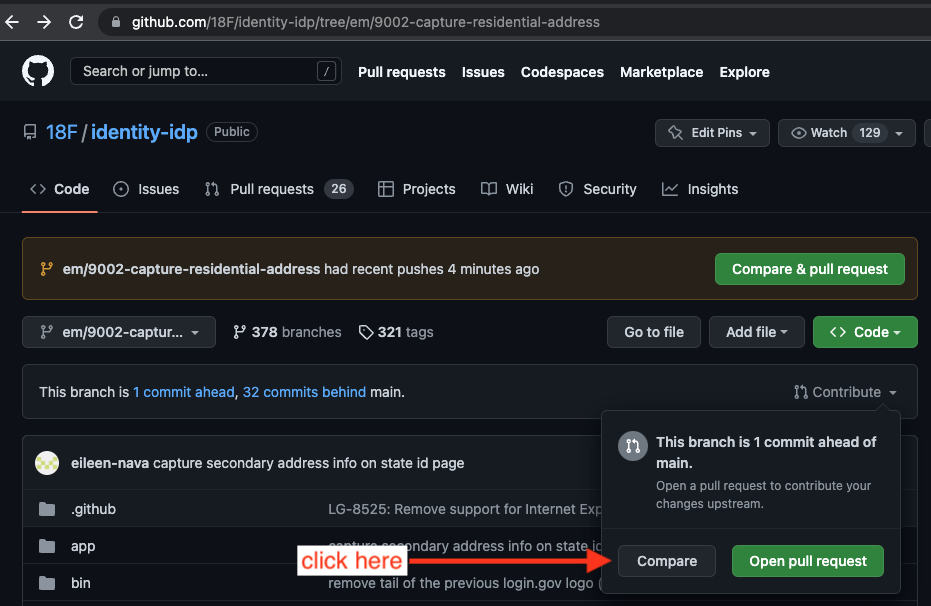
- Share the resulting url, eg https://github.com/18F/identity-idp/compare/branch-name-goes-here, with your fellow engineer.
Additionally, you can use a script like git-cmp that allows you to generate github compare urls from local branches.
 Handbook
Handbook