Background Jobs: RISC Ruby Workers
Overview
Our implementation of RISC Security Event Token uses HTTP Push (basically webhooks) to deliver notifications to partners
To minimize the impact of external HTTP requests on our application performance, we moved those calls to background jobs.
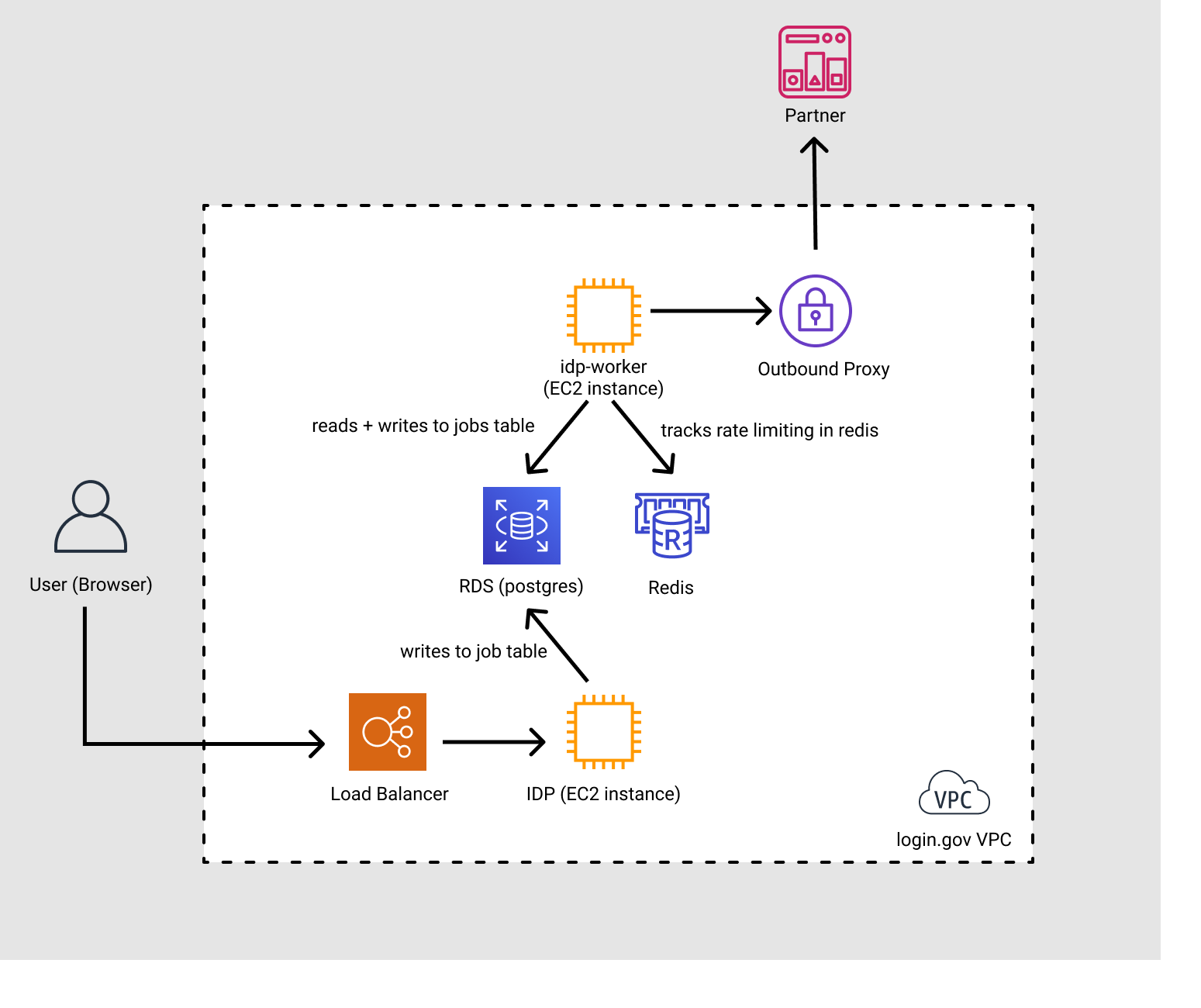 (to update this diagram, edit the Async Architecture file in Figma and re-export it)
(to update this diagram, edit the Async Architecture file in Figma and re-export it)
The lifecycle of a job:
- User performs an action that triggers a notification (such as changing their MFA)
- IdP enqueues a job
- The JWT payload is constructed and signed in the foreground, and the entire payload body is persisted temporarily as a job argument
- See data for payload contents
- Worker host picks up the job and sends it
- If the request to the partner fails, the request will be retried about 5x
Data
The jobs deliver JWT payloads which are base64-encoded and signed JSON objects (signed, not encrypted).
The data contained in the JWT payloads:
- Agency-specific UUID
- Timestamp
- Event name
- User Email (only sent for one type of event, not all events)
See the full list of supported events and example payloads
Deploys
The code for the workers lives in the same repository as the IdP, but is deployed to separate worker instances.
Configuration
-
Do the steps in Ruby Proofing Workers for job host configuration
-
Additionally update the environment’s
application.yml- set push_notifications_enabled:
'true'(this enables sending SET tokens)
- set push_notifications_enabled:
 Handbook
Handbook