IDP Artifacts
Overview
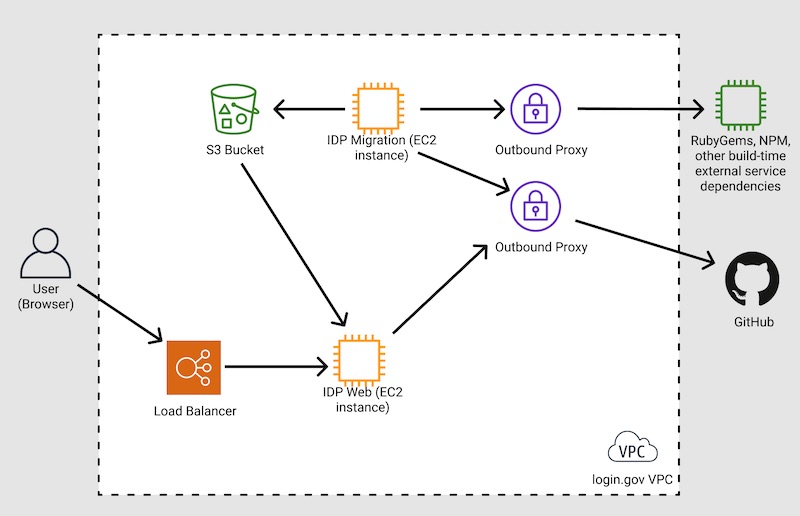
To reduce operational complexity and minimize deployment time, artifacts for IdP hosts are built in migration hosts. The artifacts consist of Login.gov’s IdP source code repositories, Ruby and Javascript dependencies downloaded via RubyGems and Node Package Manager (NPM), and compiled frontend assets. This functionality is currently backwards compatible, and deployments will fall back to existing behavior if an artifact is not available.
 (to update this diagram, edit the IDP artifact-building architecture file in Figma and re-export it)
(to update this diagram, edit the IDP artifact-building architecture file in Figma and re-export it)
Building and Uploading Artifacts
Artifacts are built within the current IdP deploy process in the migration instance. The steps are:
- Download latest IdP SHA from the configured deploy branch from GitHub
- Skip if artifact already exists for that SHA in S3
- Clone IdP on configured branch
- Run IdP deploy build script, which downloads Ruby/Javascript dependencies, and builds frontend assets
- Cache gem bundle
- Tar and GZip IdP directory into a single compressed file, excluding large static files, private configuration, and application secrets
- Upload file artifact to S3 with the SHA of the IdP git repository
Downloading Artifacts
Artifacts are only used by migration and idp instances. They will attempt to download and use artifacts following these steps:
- Download latest IdP SHA from the configured deploy branch from GitHub
- Download artifact with that SHA from S3
- Unzip artifact file into directory
- Run IdP deploy build in local-dependency mode, which explicitly disallows contacting RubyGems and NPM
Interaction with CloudFront Static Assets
Artifact generation is compatible with environments where regardless of whether CloudFront is used to serve static assets.
 Handbook
Handbook